| Name | The Machine |
| Also known as | Northern Lights |
| First Appearance | “Pilot” |
| Created by | Harold Finch Nathan Ingram |
| Purpose | Mass surveillance system |
| Status | Active |
| Active since | February 24, 2005 |
| Owned by | U.S. Government (Former) IFT (Former) |
| Location | Unknown, (previously Hanford Nuclear Reservation, Hanford, WA) |
The Machine is a computer system built and designed by Harold Finch and Nathan Ingram for a secret entity of the United States government, known by the project name "Northern Lights".
The Machine analyzes feeds from domestic organizations such as the National Security Agency, and foreign entities including Interpol (“No Good Deed”) to predict terrorist attacks and modify intelligence reports to include "relevant" data that will allow the government to forestall terrorist activity. Combined with data collected from various other sources, such as video footage, phone calls (landline, VOIP, mobile), GPS, electronic transactions, e-mails and other social media, it is able to accurately predict violent acts without anyone knowing about its existence.
Development
- Main article: The Machine/History
After September 11, 2001, Congress created the cabinet-level Department of Homeland Security via the Patriot Act giving DHS and its affiliated agencies the right to read emails and monitor phone calls. To handle the data, they needed a computer system that could scan through all the information and identify terrorists before they could act. After trials with projects like Trailblazer, TIA, and Stellar Wind were unsuccessful, the Machine was commissioned. (“No Good Deed”) Development was handed over to Nathan Ingram's company, IFT. When the Machine was completed, Ingram sold it to the government for $1.00. (“Super”) The Machine went online on February 24, 2005. (“Wolf and Cub”)
Classification of Data
The Machine sorts through all available information and categorizes persons of interest into relevant (national security) and irrelevant (everything else) cases. When a relevant threat has been identified, the information is forwarded to the NSA or the FBI (“Pilot”), without leaving any indication as to where the information originated. (“No Good Deed”)
Every night at midnight, the Machine deletes the list of irrelevant numbers: violent crimes, domestic violence or other premeditated acts that do not threaten national security. Finch later comes to believe that the irrelevant list is as important as the relevant list after Ingram dies in a violent event deemed irrelevant by the Machine. Finch therefore utilizes a back door into the Machine originally put in place by Ingram in order to access the irrelevant list.
The Machine categorizes each POI based on their actions to determine whether they are the victim or the perpetrator. (“Nothing to Hide”)

Analysis of Wayne Kruger (“Nothing to Hide”)
| VICTIM | PERPETRATOR |
|---|---|
| Opposition | Motivation |
| Locatability | Predisposition |
| Mobility | Acquisition |
| Proximity | Proximity |
| Defensibility | Capability |
| Assistance | Resistance |
Access
The current location of the Machine remains unknown. After it was handed over to the government, it was shipped from Des Moines, Iowa to Salt Lake City, Utah, then to its final location further west. (“Bad Code”) Finch stated on several occasions that he has no way of accessing the Machine, and that he also doesn’t know where it is located. (“Pilot”) (“No Good Deed”) (“The Contingency”) However, after speaking with Northern Lights engineer Lawrence Szilard, he admits he can lead Root to where it is located. (“God Mode”)
Ingram, who was looking for the Machine at one time, was able to pinpoint three likely locations, each of them U.S. nuclear processing facilities, that Northern Lights could potentially use to house The Machine. Other clues allow Root, Finch, Reese and Shaw to single out a nuclear facility in Hanford, Washington. Upon their arrival, they discover that engineers shipped it away—node by node to an unknown location, supposedly on the orders of the Special Counsel, who denied giving the orders. (“God Mode”) Using the source code from the Ordos Laptop on which Decima Technologies built its virus, Finch was able to teach the Machine to protect itself by ordering its own relocation. It remains to be seen whether the Machine's component nodes are stored in one place or distributed over multiple locations.
According to Finch, the Machine has been coded so that it cannot be altered in any way unless an individual has physical access to its hardware (“Bad Code”) or in response to a cyber-attack. (“God Mode”) It is able to update, maintain, and repair itself. (“No Good Deed”) The Machine was programmed to delete its memory every night at midnight, and then reinstantiate and rebuild itself. Because of this, it has no stored memory other than its basic programming and only has a database to process. To work around this problem, the Machine established the false human identity Ernest Thornhill, a technology millionaire. Using this identity, it set up a company and hired employees to reenter the coded memories it prints out each night. With the virus slowly infecting it, the Machine also had Ernest Thornhill buy pay phone companies all over New York City. (“Zero Day”)
The Machine contacts Finch, or in a few cases Reese, when it perceives a threat it regards as irrelevant yet imminent. It is unclear to what extent the Machine is self-aware or how far Finch is able to control it. Flashbacks indicate that the Machine once took an active interest in safeguarding Finch, but he has since set limits on such conduct. (“The High Road”) Finch is adamant that the Machine has no form of remote access, as it could be used by a hacker to gain control. (“The Contingency”)

Under certain circumstances, the system administrator (Finch) or a recognized asset (Reese) can communicate with the Machine by talking into any security or traffic camera. (“Firewall”), (“The Contingency”) The cameras flash a red light to indicate that the Machine is consequently processing the request. The Machine responds via pay phones or mobile phones.
Assessment
- Main article: The Machine/Assessment
The Machine uses various "machine learning" techniques to determine the identity, location, and intentions of monitored people.
Communication
- For a list of messages relayed by the Machine, see List of the Machine's Messages
Primary Operations
The Machine inserts relevant information (by way of a subject's Social Security number) into briefing reports destined for FBI or NSA executives. While most believe the information to be the work of various intelligence agencies, some are aware that the numbers are gathered by special means, referring to this entity as "Research".
After Vigilance leaked documents regarding Northern Lights, the governmental agencies involved have severed their link with the machine, believing to have shut it down, and have ceased operations which act on relevant numbers. These operations have been re-assigned to the Analog Interface (Root). (“Most Likely To...”)
Contingency (Secondary Operations)

The "Contingency" routine is an additional function added by Nathan Ingram just before the Machine was shut down and packed for transport. (“No Good Deed”) Initially unknown to Finch, Ingram created this function to gain access to those numbers that were sorted out as non-relevant. Shortly after the Machine left IFT, the Machine sent the first irrelevant number to Ingram. (“One Percent”)
Finch found out about Contingency in 2010 (Day 3178, or September 13). When confronted by Finch, Ingram admitted that he received numbers from the Machine, allowing him to save five of the twelve reported up to that point. Finch insisted that they should not play God and tried to delete Contingency. However, this wasn't possible, so Finch deleted Ingram's status as an auxiliary administrator and halted Contingency's processes. (“God Mode”) Finch reactivated Contingency the night after Ingram's death (Day 3191, or September 26), having observed that the Machine had classified Ingram's murder as "non-relevant". Finch reprogrammed the Contingency function so that instead of issuing the POI's social security number directly, the number was coded to the Dewey Decimal System utilizing books found in The Library and communicated via public pay phones.

Ingram's Phone
The "Irrelevant" List
The Machine uses a code based on the Dewey Decimal System to communicate the Social Security numbers of non-relevant persons of interest to Finch by phone (call or text message). (“The Contingency”) He receives coded titles and authors' initials of books that are cataloged by the DDS. (“No Good Deed”) Combining their DDS numbers allows him to put together the SSN.
Tertiary Operations
After its hard reset in the late night of April 30 (Day 4138), the Machine created a third category of numbers for what it terms Tertiary Operations (“Root Path (/)”). The Machine has only directly told Root about these people. Root's kidnap and temporary use of Shaw to rescue one of them enabled Finch and Reese to learn of this new category. (“Mors Praematura”)

(“Root Path (/)”)
Virus
Following orders from a mysterious third party, Kara Stanton uploads a virus onto the internet (“Dead Reckoning”) which initially seems to affect the Machine in such a way that it fails to send some of the numbers to Finch in time. (“Proteus”)
Finch monitors the virus's progress over time, as he tries to trace it. Eventually, it becomes apparent the Machine's output is becoming erratic, and in time, that numbers are being delayed. The delayed generation of numbers leads to the deaths of Alan Fahey, Cal Beecher, Bill Szymanski, and Dr. Richard Nelson. Along with the increasing flashes of coded blue screen, the delays suggest that the Machine might be failing. As Zero Day for the virus approaches, The Machine begins to be overwhelmed by a deluge of false data and stops issuing numbers, leading to a sharp increase in successful premeditated homicides within the city.
Glitches
- Main article: List of Embedded Codes
Over the course of “In Extremis”, the Machine experiences a number of glitches as blue screens constantly interrupt its perspective on video feeds. At the end of the episode, as the virus begins its attack on the Machine, the monitoring boxes begin to dance across the screen and disappear as the picture degrades. Finally, the Machine displays a red coded screen stating that the signal is corrupted, followed by a series of messages, each originally dissolving from western to Greek characters as its primary operations shut down:

By “Zero Day”, neither the government nor Finch have received a number for ten days. However, it appears that the Machine is still generating the irrelevant list, as it tries to contact Finch after determining that Carter may be in danger. The Machine also sends Finch the Social Security number of its fake human identity, Ernest Thornhill, thus revealing its daily activity reentering memories.
Debug Mode
The true nature of the virus is to crash the Machine with false data and trigger a "hard reset", after which the Machine reboots and calls a pay phone located in the New York Public Library, seeking admin support. At the very end of the reboot process, The Machine displays binary machine language code that translates to Latin "Quis custodiet ipsos custodes?" or "Who will watch the watchmen?"
The person who answers The Machine's call is given full admin access to the Machine for 24 hours, which Root refers to as "God Mode". By splicing the telephone lines, however, the call can be directed to more than one pay phone at once, allowing whoever answers the second phone to be given access as well. Once the 24 hours are up, their admin access is removed and they have no further communications with the Machine. (“God Mode”) (“Zero Day”)
People Who Know About the Machine
Prior to the inception of the Machine, there were seven people aware of Northern Lights, and who worked on different facets of the production and logistics. This group was classified top secret. The identities of five of the original seven are known:
In actuality, there were eight people who knew about the Machine. Denton Weeks contracted with Nathan Ingram for his company to develop the technology behind the Machine and the construction of the physical system. Ingram secretly brought Finch into the process as he was not personally capable of completing the project on his own. Finch's identity and participation was known only to Ingram.
Others came to know about the Machine later:
- Ross Garrison: Brought into the project to oversee it after the Machine's development (“Deus Ex Machina”)
- Lawrence Szilard: Oversaw the construction of the Machine's original housing (“God Mode”)
- Daniel Aquino: Built the housing for the Machine and had some knowledge of it. (“Relevance”)
- John Reese: Learned about the Machine when be began working with Finch (“Pilot”)
- Root: Learned about the Machine at an undetermined point in time, likely when she hacked Finch's network (“Root Cause”) (“Firewall”) (“The Contingency”)
- Henry Peck: Speculated the Machine had been built; suspicions later confirmed by Finch (“No Good Deed”)
- Sameen Shaw: Learned about the Machine from Reese and discusses it with him after the reset (“God Mode”)
- Hersh: Originally appointed a white square which became yellow after he took over Special Counsel's role (“God Mode”)
- A caretaker: Although it is unknown whether he knew what he was assigned to guard. (“God Mode”)
- Joss Carter: Figured out on her own after working with Finch for some time; suspicions later confirmed by Finch (“The Crossing”)
- Arthur Claypool: Learned about the Machine from Finch (“Aletheia”)
- John Greer: The conversation with Root indicates he knows about the Machine (“Allegiance”)
- Peter Collier: The conversation with Finch indicates he knows about the Machine (“Most Likely To...”)
- Daniel Casey, Jason Greenfield, Daizo: Root has told them about the Machine at some time in their involvement with her, as is apparent when the Machine categorizes them with yellow box. (“A House Divided”)
- Vigilance members, 12 jurors, reporters, and a defense attorney at the kangaroo court: Finch confirms the existence of the Machine and how it operates in order to prevent Control's execution. The Machine does not assign yellow boxes because we are seeing them from Samaritan's POV. Few if any survive the explosion in the courthouse. (“Deus Ex Machina”)
- Jeremy Lambert: speaks directly to the Machine in “The Cold War”
- Martine Rousseau: discusses the Machine with Greer and Lambert (“The Cold War”)
- Gabriel Hayward: Samaritan's interface talks about the Machine with Root (“The Cold War”)
Colored Boxes and Symbols
People
The Machine applies differently colored boxes in order to categorize the people it observes. Boxes can change as the Machine re-evaluates its assessment of the individuals it monitors.
| White box: Individuals the Machine is currently monitoring, but who do not pose an immediate threat. | |
| White box with red corners and crosshairs: Indicates imminent/ongoing violence by the indicated individual. | |
| Red box: Relevant threats and individuals who pose a threat to the Machine or one of its administrators. | |
| Yellow box: Individuals who know about the Machine. | |
| Black box with yellow corners and crosshairs: Individuals who know about the Machine and communicate with it. The Machine designates these individuals as an "analog interface". Root is the only known analog interface now. | |
| Blue box: Members of government teams; the scope of this box is unclear, but includes agents acting on "relevant" numbers. |

The boxes for Fusco (white because he doesn't know about the Machine) and Reese (yellow because he knows) turn red after the Machine learns that they were investigating Finch. (“Wolf and Cub”)
Wheeled vehicles (such as cars, trucks and buses) are coded based on status of individual passengers within.
| Starting in Season 3, the boxes are slightly modified to have solid vertical lines rather than dashed ones, along with a central target identifying the vehicle being monitored. |
Watercraft and Aircraft
The Machine also categorizes and marks watercraft and aircraft.
| Boats, ships and ferries are assigned a white diamond. (Seasons 1 and 2) | |
| In Season 3, this was modified to have solid lines instead of dashed ones from the left and right corners to the crosshairs above and below them, with a central target similar to that of the vehicle box. | |
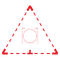
| Airplanes and helicopters under normal operation receive a green triangle along with flight number and airport codes. | |
| Aircraft under imminent threat or transporting software considered a threat to the Machine are assigned a red triangle instead of green. (“4C”) (“RAM”) |
The Machine can also recognize celestial objects such as Mars, (“God Mode”) and can access satellite imagery to track air traffic or individual planes.
Exclusion Zones

Freedom Tower
The Machine monitors areas around potential terrorist targets, such as sky lanes, shipping lanes, and major railroads. (“Dead Reckoning”) Exclusion zones are coded in white or red, which may represent a threat appraisal, or the value of the target.
Notes
- The producers' commentary on the Season 1 DVD confirms that in flashbacks, the Machine reviews old footage in the present, meaning that it assigns the colored squares according to what it knows about the characters in the current timeline. Therefore, the yellow square it assigned Reese in various flashbacks before Finch told him about the Machine may only indicate that the Machine uses a present day indicator, not that Reese knew about the Machine before meeting Finch.
- Palantir, a CIA-funded enterprise software company whose name comes from the seeing stones in J. R. R. Tolkien's fantasy epic The Lord of the Rings bears an eerie resemblance to the Machine. Since its development in 2004, the software has been able to locate terrorists, prevent bank fraud and track disease outbreaks using data-mining tools that allow users to comb through and make connections in massive sets of widely disparate data. Palantir is able to "learn" when new data is uploaded to its huge server farms. U.S. military intelligence has used Palantir to improve their ability to predict locations of Improvised Explosive Devices in Afghanistan. Palantir has been valued at between $5 to $8 billion.
- The Domain Awareness System created by the NYPD in conjunction with Microsoft at a cost of $40 million has some similarities to the Machine. The Domain Awareness System was profiled in an episode of Nova about the hunt for the Boston Marathon bombers. The system has been referenced several times in the series: in “In Extremis”, IAB uses satellite photos from Domain Awareness to identify possible gravesites where Detective Stills might be buried; in “Reasonable Doubt”, it is used to track Scott Rollins' stolen SUV; and in “Razgovor”, it is mentioned that funding ran out for the project in the run-down area where Genrika Zhirova lived.
Trivia
- The extent of Nathan Ingram's contingency protocol inside the Machine is unknown. During Finch's absence (“The Contingency”) the Machine tasked Reese with the job of searching and protecting the numbers that came up, thus implying that Reese or any immediate asset are part of that contingency.
- In “Relevance”, the Machine is referred to as "Research" by Sameen Shaw and Michael Cole, as it provides them the SSNs from the relevant list. However, in the first encounter between Shaw and Finch, she is informed by Finch that "Research" is non-existent but full of secrecy, but that ultimately they both work for the same entity.
- The Machine is stored on IFT Sabre Blade 2437 servers which are renamed Dell PowerEdge SC1425 servers. (“Pilot”) (“Ghosts”)
- During the episode "Prophets" a previous generation of The Machines source code was shown on screen. The source code displayed was that of the Stuxnet worm.